A best online resource to prepare for the EC-COUNCIL 312-50V11 exam: latest 312-50V11 practice test. The latest 312-50V11 exam dumps pdf. Pass4itsure full 312-50V11 dumps https://www.pass4itsure.com/312-50v11.html (Total Questions: 429 Q&A 312-50V11 Dumps Pdf) can help you pass your first exam!
New 2021 EC-COUNCIL 312-50V11 dumps pdf from google drive (Update Questions)
Welcome to download [free questions] EC-COUNCIL 312-50V11 dumps pdf https://drive.google.com/file/d/1IxAGuyTjJMGfwsYam92KSkIesjNca1RF/view?usp=sharing
New EC-COUNCIL 312-50V11 exam practice questions(q1-q13)
QUESTION 1
There are multiple cloud deployment options depending on how isolated a customer\\’s resources are from those of
other customers. Shared environments share the costs and allow each customer to enjoy lower operations expenses.
One solution Is for a customer to Join a group of users or organizations to share a cloud environment. What is this
cloud deployment option called?
A. Hybrid
B. Community
C. Public
D. Private
Correct Answer: C
QUESTION 2
in this attack, an adversary tricks a victim into reinstalling an already-in-use key. This is achieved by manipulating and
replaying cryptographic handshake messages. When the victim reinstall the key, associated parameters such as the
incremental transmit packet number and receive packet number are reset to their initial values. What is this attack
called?
A. Chop chop attack
B. KRACK
C. Evil twin
D. Wardriving
Correct Answer: B
In this attack KRACK is an acronym for Key Reinstallation Attack. KRACK may be a severe replay attack on Wi-Fi
Protected Access protocol (WPA2), which secures your Wi-Fi connection. Hackers use KRACK to take advantage of a
vulnerability in WPA2. When in close range of a possible victim, attackers can access and skim encrypted data using
KRACK. How KRACK WorksYour Wi-Fi client uses a four-way handshake when attempting to attach to a protected
network. The handshake confirms that both the client — your smartphone, laptop, et cetera — and therefore the access
point share the right credentials, usually a password for the network. This establishes the Pairwise passkey (PMK),
which allows for encoding .Overall, this handshake procedure allows for quick logins and connections and sets up a
replacement encryption key with each connection. this is often what keeps data secure on Wi-Fi connections, and every
one protected Wi-Fi connections use the four-way handshake for security. This protocol is that the reason users are
encouraged to use private or credential-protected Wi-Fi instead of public connections.KRACK affects the third step of
the handshake, allowing the attacker to control and replay the WPA2 encryption key to trick it into installing a key
already in use. When the key\\’s reinstalled, other parameters related to it — the incremental transmit packet number
called the nonce and therefore the replay counter — are set to their original values.Rather than move to the fourth step
within the four-way handshake, nonce resets still replay transmissions of the third step. This sets up the encryption
protocol for attack, and counting on how the attackers replay the third- step transmissions, they will take down Wi-Fi
security. Why KRACK may be a ThreatThink of all the devices you employ that believe Wi-Fi. it isn\\’t almost laptops
and smartphones; numerous smart devices now structure the web of Things (IoT). due to the vulnerability in WPA2,
everything connected to Wi-Fi is in danger of being hacked or hijacked.Attackers using KRACK can gain access to
usernames and passwords also as data stored on devices. Hackers can read emails and consider photos of transmitted data then use that information to blackmail users or sell it on the Dark Web.Theft of stored data requires more steps, like
an HTTP content injection to load malware into the system. Hackers could conceivably take hold of any device used
thereon Wi-Fi connection. Because the attacks require hackers to be on the brink of the target, these internet security
threats could also cause physical security threats.On the opposite hand, the necessity to be in close proximity is that the
only excellent news associated with KRACK, as meaning a widespread attack would be extremely difficult.Victims are
specifically targeted. However, there are concerns that a experienced attacker could develop the talents to use HTTP
content injection to load malware onto websites to make a more widespread affect. Everyone is in danger from KRACK
vulnerability. Patches are available for Windows and iOS devices, but a released patch for Android devices is currently
in question (November 2017). There are issues with the discharge , and lots of question if all versions and devices are
covered.The real problem is with routers and IoT devices. These devices aren\\’t updated as regularly as computer
operating systems, and for several devices, security flaws got to be addressed on the manufacturing side. New devices
should address KRACK, but the devices you have already got in your home probably aren\\’t protected. The best
protection against KRACK is to make sure any device connected to Wi-Fi is patched and updated with the newest
firmware. that has checking together with your router\\’s manufacturer periodically to ascertain if patches are available.
The safest connection option may be a private VPN, especially when publicly spaces. If you would like a VPN for private
use, avoid free options, as they need their own security problems and there\\’ll even be issues with HTTPs. Use a paid
service offered by a trusted vendor like Kaspersky. Also, more modern networks use WPA3 for better security.Avoid
using public Wi-Fi, albeit it\\’s password protection. That password is out there to almost anyone, which reduces the
safety level considerably.All the widespread implications of KRACK and therefore the WPA2 vulnerability aren\\’t yet
clear. what\\’s certain is that everybody who uses Wi-Fi is in danger and wishes to require precautions to guard their
data and devices.
QUESTION 3
Kevin, a professional hacker, wants to penetrate CyberTech Inc.\\’s network. He employed a technique, using which he
encoded packets with Unicode characters. The company\\’s IDS cannot recognize the packet, but the target web server
can decode them.
What is the technique used by Kevin to evade the IDS system?
A. Desynchronization
B. Obfuscating
C. Session splicing
D. Urgency flag
Correct Answer: B
Explanation: Adversaries could decide to build an possible or file difficult to find or analyze by encrypting, encoding, or
otherwise obfuscating its contents on the system or in transit. this is often common behavior which will be used across
totally different platforms and therefore the network to evade defenses. Payloads may be compressed, archived, or
encrypted so as to avoid detection. These payloads may be used throughout Initial Access or later to mitigate detection.
typically a user\\’s action could also be needed to open and Deobfuscate/ Decode Files or info for User Execution. The
user can also be needed to input a parole to open a parole protected compressed/encrypted file that was provided by
the mortal. Adversaries can also used compressed or archived scripts, like JavaScript. Portions of files can even be
encoded to cover the plain-text strings that will otherwise facilitate defenders with discovery. Payloads can also be split
into separate, ostensibly benign files that solely reveal malicious practicality once reassembled. Adversaries can also
modify commands dead from payloads or directly via a Command and Scripting Interpreter. surroundings variables,
aliases, characters, and different platform/ language specific linguistics may be wont to evade signature based mostly
detections and application management mechanisms.
QUESTION 4
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which
TCP and UDP ports must you filter to check null sessions on your network?
A. 137 and 139
B. 137 and 443
C. 139 and 443
D. 139 and 445
Correct Answer: D
QUESTION 5
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that allows session
oriented connections (Telnet) and performs the sequence prediction on the target operating system. He manages to find
an active session due to the high level of traffic on the network. What is Bob supposed to do next?
A. Take over the session
B. Reverse sequence prediction
C. Guess the sequence numbers
D. Take one of the parties offline
Correct Answer: C
QUESTION 6
Yancey is a network security administrator for a large electric company. This company provides power for over 100, 000
people in Las Vegas. Yancey has worked for his company for over 15 years and has become very successful. One day,
Yancey comes in to work and finds out that the company will be downsizing and he will be out of a job in two weeks.
Yancey is very angry and decides to place logic bombs, viruses, Trojans, and backdoors all over the network to take
down the company once he has left. Yancey does not care if his actions land him in jail for 30 or more years, he just
wants the company to pay for what they are doing to him.
What would Yancey be considered?
A. Yancey would be considered a Suicide Hacker
B. Since he does not care about going to jail, he would be considered a Black Hat
C. Because Yancey works for the company currently; he would be a White Hat
D. Yancey is a Hacktivist Hacker since he is standing up to a company that is downsizing
Correct Answer: A
QUESTION 7
Which of the following algorithms can be used to guarantee the integrity of messages being sent, in transit, or stored?
A. symmetric algorithms
B. asymmetric algorithms
C. hashing algorithms
D. integrity algorithms
Correct Answer: C
QUESTION 8
Which of the following tools are used for enumeration? (Choose three.)
A. SolarWinds
B. USER2SID
C. Cheops
D. SID2USER
E. DumpSec
Correct Answer: BDE
QUESTION 9
Eric has discovered a fantastic package of tools named Dsniff on the Internet. He has learnt to use these tools in his lab
and is now ready for real world exploitation. He was able to effectively intercept communications between the two
entities and establish credentials with both sides of the connections. The two remote ends of the communication never
notice that Eric is relaying the information between the two. What would you call this attack?
A. Interceptor
B. Man-in-the-middle
C. ARP Proxy
D. Poisoning Attack
Correct Answer: B
QUESTION 10
Peter, a Network Administrator, has come to you looking for advice on a tool that would help him perform SNMP
enquires over the network.
Which of these tools would do the SNMP enumeration he is looking for? Select the best answers.
A. SNMPUtil
B. SNScan
C. SNMPScan
D. Solarwinds IP Network Browser
E. NMap
Correct Answer: ABD
QUESTION 11
Elliot is in the process of exploiting a web application that uses SQL as a back-end database. He\\’s determined that the
application is vulnerable to SQL injection, and has introduced conditional timing delays into injected queries to
determine whether they are successful. What type of SQL injection is Elliot most likely performing?
A. Error-based SQL injection
B. Blind SQL injection
C. Union-based SQL injection
D. NoSQL injection
Correct Answer: B
QUESTION 12
Study the following log extract and identify the attack.
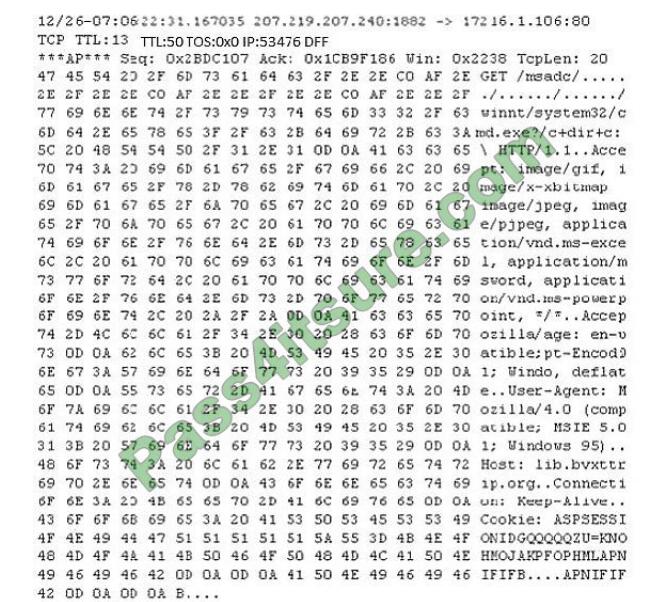
A. Hexcode Attack
B. Cross Site Scripting
C. Multiple Domain Traversal Attack
D. Unicode Directory Traversal Attack
Correct Answer: D
QUESTION 13
An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious sequence of packets
sent to a Web server in the network\\’s external DMZ. The packet traffic was captured by the IDS and saved to a PCAP
file. What type of network tool can be used to determine if these packets are genuinely malicious or simply a false
positive?
A. Protocol analyzer
B. Network sniffer
C. Intrusion Prevention System (IPS)
D. Vulnerability scanner
Correct Answer: A
Pass4itsure EC-COUNCIL dumps discount code 2021 free share

The last sentence:
This blog shares the latest EC-COUNCIL 312-50V11 exam questions, and answers! EC-COUNCIL 312-50V11 pdf, EC-COUNCIL 312-50V11 exam video! Get full Pass4itsure 100% pass & stable EC-COUNCIL 312-50V11 dumps!
ps.
Latest update EC-COUNCIL 312-50V11 exam dumps: https://www.pass4itsure.com/312-50v11.html
[PDF] Free EC-COUNCIL 312-50V11 pdf: https://drive.google.com/file/d/1IxAGuyTjJMGfwsYam92KSkIesjNca1RF/view?usp=sharing