The EC-COUNCIL 312-50V11 exam, or Certified Ethical Hacker v11 exam, is not simple. If you don’t get into the habit of learning every day and have confidence in yourself and find the right EC-COUNCIL 312-50V11 exam dumps questions, it’s impossible to pass this exam. Obtain the appropriate 312-50v11 question material during the preparation process, and Certificationvce assures you that you will not regret it.
This blog post, not only tells you how to pass the exam but also shares some of the questions of the EC-COUNCIL 312-50V11 exam dumps for you to practice, of course, the complete need for your purchase, you can try it first, fit, you are considering buying.
PS, full EC-COUNCIL 312-50V11 exam dumps link here: https://www.pass4itsure.com/312-50v11.html PDF and VCE formats of your choice!
EC-COUNCIL 312-50v11 actual exam questions, answers and explanations for free
QUESTION 1 #
Which of the following describes the characteristics of a Boot Sector Virus?
A. Modifies directory table entries so that directory entries point to the virus code instead of the actual program.
B. Moves the MBR to another location on the RAM and copies itself to the original location of the MBR.
C. Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR.
D. Overwrites the original MBR and only executes the new virus code.
Correct Answer: C
QUESTION 2 #
Harper, a software engineer, is developing an email application. To ensure the confidentiality of email messages,
Harper uses a symmetric-key block cipher having a classical 12- or 16-round Feistel network with a block size of 64 bits for encryption, which includes large 8 × 32-bit S-boxes (S1, S2, S3, S4) based on bent functions, modular addition, and subtraction, key-dependent rotation, and XOR operations.
This cipher also uses a masking key (Km1) and a rotation key (Kr1) for performing its functions.
What is the algorithm employed by Harper to secure the email messages?
A. CAST-128
B. AES
C. GOST block cipher
D. DES
Correct Answer: A
QUESTION 3 #
Shiela is an information security analyst working at HiTech Security Solutions. She is performing the service version discovery using Nmap to obtain information about the running services and their versions on a target system.
Which of the following Nmap options must she use to perform service version discovery on the target host?
A. -sN
B. -sV
C. -sX
D. -sF
Correct Answer: B
QUESTION 4 #
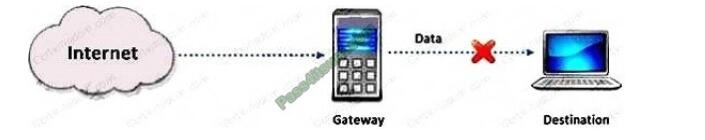
John, a professional hacker, decided to use DNS to perform data exfiltration on a target network, in this process, he embedded malicious data into the DNS protocol packets that even DNSSEC cannot detect.
Using this technique. John successfully injected malware to bypass a firewall and maintained communication with the victim machine and CandC server. What is the technique employed by John to bypass the firewall?
A. DNS cache snooping
B. DNSSEC zone walking
C. DNS tunneling method
D. DNS enumeration
Correct Answer: C
DNS tunneling may be a method wont to send data over the DNS protocol, a protocol that has never been intended for data transfer. due to that, people tend to overlook it and it\’s become a well-liked but effective tool in many attacks.
The most popular use case for DNS tunneling is obtaining free internet through bypassing captive portals at airports, hotels, or if you are feeling patient the not-so-cheap on the wing Wi-Fi. On those shared internet hotspots HTTP traffic is blocked until a username/password is provided, however DNS traffic is usually still allowed within the background:
we will encode our HTTP traffic over DNS and voil? we\’ve internet access. This sounds fun but the reality is, browsing anything on DNS tunneling is slow. Like, back to 1998 slow. Another more dangerous use of DNS tunneling would be bypassing network security devices (Firewalls, DLP appliances…) to line up an immediate and unmonitored communications channel on an organization \’s network.
Possibilities here are endless: Data exfiltration, fixing another penetration testing tool… you name it. To make it even more worrying, their \’s an outsized amount of easy-to-use DNS tunneling tools out there.There\’s even a minimum of one VPN over DNS protocol provider (warning: the planning of the website is
hideous, making me doubt the legitimacy of it).
As a pentester, all this is often great, as a network admin, not such a lot. How does it work: For those that ignoramus about DNS protocol but still made it here, I feel you deserve a really brief on what DNS does: DNS is sort of a phonebook for the web, it translates URLs (human-friendly language, the person\’s name), into an IP address (machine-friendly language, the phone number).
That helps us remember many websites, same as we will remember many people\’s names. For those that know what DNS is I might suggest looking here for a fast refresh on DNS protocol, but briefly what you would like to understand is:?A Record: Maps a website name to an IP address.example.com?
12.34.52.67?NS Record (a.k.a. Nameserver record): Maps a website name to an inventory of DNS servers, just in case our website is hosted in multiple servers.example.com? server1.example.com, server2.example.com who is involved in DNS tunneling?? Client. Will launch DNS requests with data in them to a website .?
One Domain that we will configure. So DNS servers will redirect its requests to an outlined server of our own.? Server. this is often the defined nameserver that can ultimately receive the DNS requests.
The 6 Steps in DNS tunneling (simplified):1. The client encodes data during a DNS request. The way it does this is often by prepending a bit of knowledge within the domain of the request.
for instance : mypieceofdata.server1.example.com2. The DNS request goes bent a DNS server.3. The DNS server finds out the A register of your domain with the IP address of your server.4.
The request for mypieceofdata.server1.example.com is forwarded to server.5. The server processes regardless of the mypieceofdata were alleged to do. Let\’s assume it had been an HTTP request.6. The server replies over DNS and Woop Woop, we\’ve got signal.
QUESTION 5 #
You are trying to break into a highly classified top-secret mainframe computer with the highest security system in place at Merclyn Barley Bank located in Los Angeles.
You know that conventional hacking doesn\’t work in this case, because organizations such as banks are generally tight and secure when it comes to protecting their systems.
In other words, you are trying to penetrate an otherwise impenetrable system.
How would you proceed?
A. Look for “zero-day” exploits at various underground hacker websites in Russia and China and buy the necessary exploits from these hackers and target the bank\’s network
B. Try to hang around the local pubs or restaurants near the bank, get talking to a poorly- paid or disgruntled employee, and offer them money if they\’ll abuse their access privileges by providing you with sensitive information
C. Launch DDOS attacks against Merclyn Barley Bank\’s routers and firewall systems using 100, 000 or more
“zombies” and “bots”
D. Try to conduct Man-in-the-Middle (MiTM) attack and divert the network traffic going to the Merclyn Barley Bank\’s Webserver to that of your machine using DNS Cache Poisoning techniques
Correct Answer: B
QUESTION 6 #
Which type of malware spreads from one system to another or from one network to another and causes similar types of damage as viruses to do to the infected system?
A. Worm
B. Rootkit
C. Adware
D. Trojan
Correct Answer: A
QUESTION 7 #
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
A. 137 and 139
B. 137 and 443
C. 139 and 443
D. 139 and 445
Correct Answer: D
QUESTION 8
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple, small-sized packets to the target computer, making it very difficult for an IDS to detect the attack signatures. Which tool can be used to perform session splicing attacks?
A. TCP splice
B. Burp
C. Hydra
D. Whisker
Correct Answer: D
QUESTION 9 #
What is correct about digital signatures?
A. A digital signature cannot be moved from one signed document to another because it is the hash of the original document encrypted with the private key of the signing party.
B. Digital signatures may be used in different documents of the same type.
C. A digital signature cannot be moved from one signed document to another because it is a plain hash of the document content.
D. Digital signatures are issued once for each user and can be used everywhere until they expire.
Correct Answer: A
QUESTION 10 #
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. You understand that all users are required to use passwords that are at least 8 characters in length.
All passwords must also use 3 of the 4 following categories: lower case letters, capital letters, numbers, and special characters.
With your existing knowledge of users, likely user account names, and the possibility that they will choose the easiest passwords possible, what would be the fastest type of password cracking attack you can run against these hash values and still get results?
A. Online Attack
B. Dictionary Attack
C. Brute Force Attack
D. Hybrid Attack
Correct Answer: D
Up-to-date Certified Ethical Hacker v11 312-50v11 exam PDF questions
312-50v11 exam PDF [Drive] free download https://drive.google.com/file/d/1Rm9K4rLH5HG74O1aSc5tHZQLP96tRi-2/view?usp=sharing
Understanding the basics of the 312-50v11 exam doesn’t mean you’ll easily pass the Certified Ethical Hacker v11 exam. In order to pass 312-50v11 with excellent results, some preparation is required. Learning through practice questions and preparing for the 312-50v11 exam dumps are the correct way to pass the exam. The good news is that Pass4itSure can help you prepare for your exam. Gain hands-on experience and practice with the help of The Pas4itSure 312-50v11 exam dumps (linked to this https://www.pass4itsure.com/312-50v11.html) training resources.
Let’s start! All the best! Remember, being the first to finish doesn’t guarantee you a passing mark but to answer the questions correctly.